by Joshua Branson ? October 25, 2025
My friend has a TalosII and a blackbird computer. He would like to update both computers' firmware. More recent version of the TalosII's firmware, allow one to navigate a web browser to https://OpenBMCIpAddress. There you can click a few buttons to update your firmware. Unfortunately, my friend is using an old firmware version that does not offer a web interface. So how can we update the firmware?
It is also useful to mention that raptor computing has developed an open source software based BMC called artic tern, which allows one to boot his raptor computer nearly instantly. If you decide to use the artic tern, then this guide will be mostly useless.
The recommended method, is to ssh into the BMC (base management controller). With power to the motherboard, but before you press the power on button, you can do something like this:
ssh root@OpenBmcIPaddress
# lots of magic commands that update the firmware
Well let's try that, but first, what's the OpenBMC's IP address? Interestingly, both the blackbird and the TalosII have multiple ethernet ports, so both machines' have multiple IP addresses. Each machine has one IP address that is exclusively used by the OpenBMC. The easiest way to find that address, is to log into the router, and select Network Settings -> LAN (we are using the turris omni router). All of the Talos II's and the Blackbird's MAC addresses start with "2c:09:4d". You then try to ssh into all of those IP addresses. One will eventually ask you for a password. Note that our blackbird's BMC's hostname was "blackbird," while the TalosII's BMC's hostname was "talos".
Unfortunately, we do not know the root password (the default password is "0penBmc" not "OpenBmc"). We tried guessing a few different potential passwords, but we have lost those the BMC's root password. That's not a problem, because there is a sneaky way to reset the root password with a serial port.
What is serial port eh (also called a com port)? Serial ports are a slightly outdated but extremely reliable protocol to communicate with a device, particularly during early boot, in this case even before you press the power button! Yes, you can use a com port to communicate with the blackboard and TalosII as soon as you plug power into the motherboard! With a serial port, one can watch the talos start U-Boot, which starts booting the OpenBMC, which eventually starts petitboot, which lets the user select the operating system to boot.
Here's an ASCII art depicting the boot up sequence:
plug in power to the motherboard
||
\/
Uboot starts ==> the com port starts working
||
\/
OpenBMC starts ==> it boots a mimimal busybox linux distro.
||
\/
petiboot starts
||
\/
The user selects which operating system to boot.Required hardware
Ok what hardware does one need to use a serial connection?
This video will tell you what hardware you need to set up the serial connection (also called a com port).
You will need to hook a serial bracket (be sure that you buy the right serial bracket: the Intel/DTK standard) to the motherboard (consult the talos and blackbird manual for where to plug this in), a null modem, and a serial to usb adapter. Do ask questions in the #talos-workstation on the OFTC network for help, which I had to many times.
If you are like me and have no idea what a serial bracket is?it looks like this:

Setting up the com port
Since I am running OpenBSD, I want to enable my regular user to use a serial connection: doas usermod -G dialer joshua. Then I plugged in the serial cord to the talos, plugged in the serial to usb adapter, and plugged the usb in my laptop.
joshua@dobby.lan:~/ $ sysctl | grep hw.ucom
hw.ucomnames=ucom0:usb5.0.00001.0Then I needed to read man cu to learn about how to establish the serial connection. You should run this command before you plug in power to the motherboard.
joshua@dobby.lan:~/ $ cu -s 115200 -l usb5.0.00001.0
The cu command is specifying connection details: "115200 8n1", which means that the speed of the connection is 115200 with 8 data bits, 1 stop bit, and flow control off and parity none.
When the OpenBMC has completely booted up, it should give you a login prompt, over the serial connection. And it should say "OpenBMC" somewhere. Mine looked like "Phosphor OpenBMC (Phosphor OpenBMC Project Reference Distro) 0.1.0 talos ttyS4". I did not know the BMC's root password, so I could not log in. I reset the BMC password, which this blog post explains better.
The first thing I did, was to disable the watchdog. Essentially, due to a rarely occurring hardware issue, Uboot tries to start the OpenBMC every 40 seconds. If you fail to run a command in that time or fail to stop the watchdog, then uboot will boot the OpenBMC.
root@talos $ loads 83000000root@talos $ # Now paste in the this binary: disable-watchdog-binaryroot@talos $ go 83000000 # this runs the program
With the watchdog disabled, I can finally reset the root password to "0penBmc".
root@talos:~/ $ printenv
baudrate=115200
bootargs=console=ttyS4,115200n8 root=/dev/ram rw
bootcmd=bootm 20080000
bootdelay=2
eth1addr=2c:09:4d:00:08:a0
ethact=aspeednic#0
ethaddr=2c:09:4d:00:08:a0
spi_dma=yes
stderr=serial
stdin=serial
stdout=serial
verify=yesI copied the value of bootargs into this next command, which I modified via adding in overlay-filesystem-in-ram. I need to run the setenv command twice. You may need to physically pull the power out of the computer and put it back in so that you can run this command twice.
root@talos:~/ $ setenv bootargs console=ttyS4,115200n8 root=/dev/ram overlay-filesystem-in-ram rw
root@talos:~/ $ setenv bootargs console=ttyS4,115200n8 root=/dev/ram overlay-filesystem-in-ram rw
root@talos:~/ $ # watchdog is now disabled! woo!
root@talos:~/ $ # let's reset the default password to 0penBmc
root@talos:~/ $ flash_eraseall /dev/mtd/rwfs
root@talos:~/ $ reboot
Now I was able to ssh root@talosIPAddress, which makes updating the firmware straightforward.
We then were able to log in to the BMC via https://BMCIpAddress. That was pretty cool. This should mean that we are able to update the firmware via the web interface? tl;dr that didn't work.
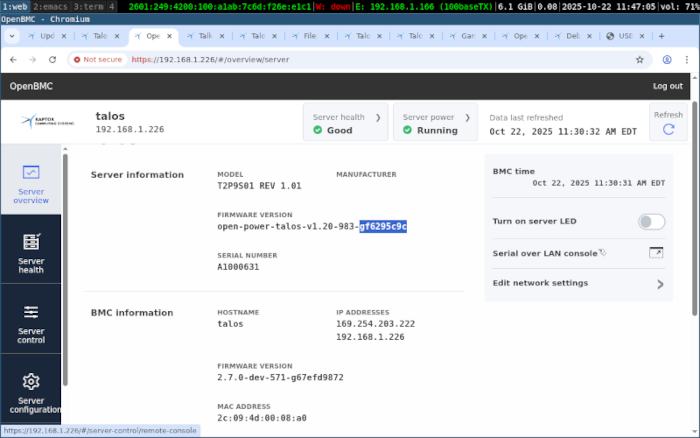
Notice the highlighted gf6295c9c text. Consulting this table, (and lots of help on irc), we confirmed that our Talos II is using firmware version 2.00, which means that our BMC is up to date, but the PNOR could be updated. I even made a short video showing my attempt to update the firmware via the web interface.
Since the web interface didn't work to update the PNOR, I went and updated the PNOR firmware via ssh.
joshua@dobby.lan:~/ $ wget \
Downloads/https://wiki.raptorcs.com/w/images/6/61/Talos-ii-pnor-v2.10-bundle.tar
Set static IP addresses on everything
So it gets really annoying to want to ssh into the blackbird's BMC, or the Talos' BMC, or debian running on the Talos, or debian running on the blackbird, to try to remember the IP addresses. It is soo much easier to make set up static IP address with your router and then set up etc/hosts.
Here's some of the static IP addresses from our router:
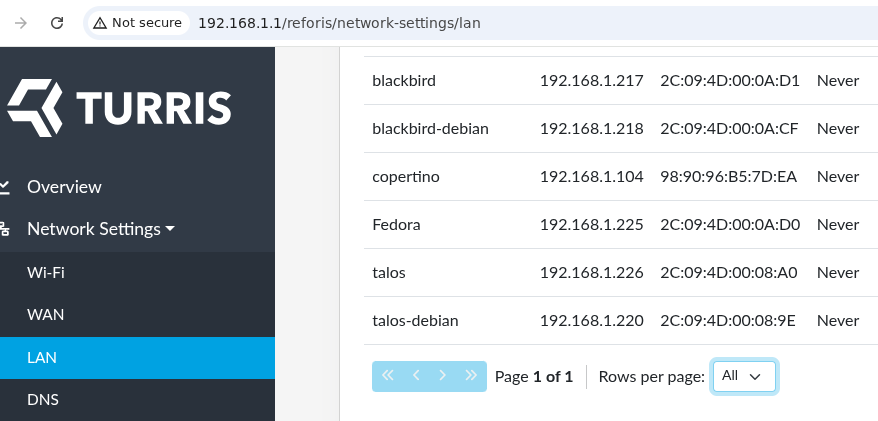
And here's my /etc/hosts/ file.
joshua@dobby.lan:~/ $ cat /etc/hosts
127.0.0.1 localhost
192.168.1.1 local.router
192.168.1.226 talos-bmc.local
192.168.1.220 talos-debian.local
192.168.1.217 blackbird-bmc.local
192.168.1.225 blackbird-fedora.local
192.168.1.218 blackbird-debian.local blackbird-devuan.local
# beaver labs guix-hosting VPS
37.59.124.162 aquinas
192.168.1.104 copertino.local
# Guix System Dell Optiplex 7010
172.16.112.28 gabriel.local
127.0.0.1 gnucode.org.local
127.0.0.1 hurdos.com.local
127.0.0.1 curiousfollowers.com.local
127.0.0.1 propernaming.org.local
127.0.0.1 gnu-hurd.com.local
127.0.0.1 local.worg.org
::1 localhostNow commands like this will just work<sup>tm</sup>
joshua@dobby.lan:~/ $ ssh root@blackbird-debian.local 'uname -a'
Linux blackbird-debian 6.12.48+deb13-powerpc64le #1 SMP Debian 6.12.48-1 (2025-09-20) ppc64le GNU/LinuxUpdating the PNOR firmware
joshua@dobby.lan:~/Downloads/ $ tar -xf Talos-ii-pnor-v2.10-bundle.tar
joshua@dobby.lan:~/Downloads/ $ # chmod u+w shell_upgrade
joshua@dobby.lan:~/Downloads/ $ bzip2 -d ./shell_upgrade/talos-ii-v2.10.pnor.bz2
joshua@dobby.lan:~/Downloads/ $ scp -O ./shell_upgrade/talos-ii-v2.10.pnor root@talos-bmc.local:/tmp/
root@talos-bmc.local:~/ $ pflash -E -p /tmp/talos-ii-v2.10.pnor
root@talos-bmc.local:~/ $ pflash -P CVPD -c
root@talos-bmc.local:~/ $ rm /tmp/talos-ii-v2.10.pnor
Updating the BMC firmware
For future reference, here is how one updates the BMC firmware. We don't need to do it, because there was no change in the BMC firmware.
joshua@dobby.lan:~/Downloads/ $ scp image-{kernel,rofs} root@$TALOS_BMC_ADDR:/run/initramfs/
root@192.168.1.226:~/ $ reboot
Updating FPGA firmware
You have to physically flash this the FPGA. It's not possible to flash this via software. The FPGA doesn't change very often, so it's not super critical is if is not updated.
Or this may help: https://forums.raptorcs.com/index.php/topic,349.msg4232.html#msg4232
https://wiki.raptorcs.com/wiki/Debricking_the_BMC#Reset_persistent_storage
<helpfulBro> regarding the flashing, IIRC buspirate was recommended as an open and cheap option for flashing the FPGA, but for writing the BMC (and PNOR) out of the system you can use any flash programmer with the right adapter (eg. TL866) <gnucode> the adapter is the TL866 ? <gnucode> I just don't know what to buy to flash the BMC and PNOR <helpfulBro> TL866 is a programmer, see eg. https://www.ebay.de/itm/376505717827, they new versions like T48, T56, ?
https://www.ebay.de/itm/376505717827
On rasberrypi OS, you'll have to enable SPI
$ sudo raspi-config
Select "Interface Options". Then select "Enable/disable automatic loading of SPI kernel module". Click "Yes".
this forum page has a link to the OpenBMC on PNOR flash chip, which should contain the massive data sheet.
I got this command from a google ai. -p ch341a_spi should actually be something like -p linux_spi:dev=/dev/
flashrom -p ch341a_spi -w filename-of-the-firmware.bin -V
This video may be helpful: https://www.youtube.com/watch?v=L35AD0LS70g
Changing BMC's root password
Obviously we want to change the BMC's root password. Otherwise, anyone who comes to my friend's house and knows his wifi password, can trivially hack into his computer. #Don'tUseDefaultPasswords!
Unfortunately the passwd command failed.
root@talos-bmc.local:/ $ passwd root
New password: ******
Retype new password: ******
passwd: Authentication token is no longer valid; new one required
passwd: password unchanged
We hate you. Your father is a ????! And your mother is a ????!After a quick searching to the AI lords, they suggested that /etc/passwd or /etc/shadow/ could be not writable.
root@192.168.1.226:~/ $ ls -lha /etc/passwd
root@192.168.1.226:~/ $ ls -lha /etc/shadow
-rw-r--r-- 1 root root 1.0K Feb 19 2020 /etc/passwd
-r-------- 1 root root 682 Oct 23 15:44 /etc/shadowWell I made /etc/shadow writable as root, but the passwd still failed.
The AI overlords then suggested that I see if there is an immutable flag on those two files with lsattr, which is not installed on the BMC's embedded linux distro.
root@192.168.1.226:/ $ lsattr /etc/passwd 2>&1
sh: line 1: lsattr: command not foundFinally the AI overlords said, "Well maybe your filesystem is full." Let's check that.
root@192.168.1.226:/ $ df -h
Filesystem Size Used Available Use% Mounted on
dev 175.9M 0 175.9M 0% /dev
tmpfs 209.2M 14.7M 194.5M 7% /run
/dev/mtdblock4 20.5M 20.5M 0 100% /run/initramfs/ro
/dev/mtdblock5 4.0M 468.0K 3.5M 11% /run/initramfs/rw
cow 4.0M 468.0K 3.5M 11% /
tmpfs 209.2M 8.0K 209.2M 0% /dev/shm
tmpfs 209.2M 0 209.2M 0% /sys/fs/cgroup
tmpfs 209.2M 4.0K 209.2M 0% /tmp
tmpfs 209.2M 24.0K 209.2M 0% /var/volatileWell that /run/initramfs/ro looks full. I started looking for large files that maybe I needed to delete.
root@192.168.1.226:/ $ du | sort -n | tail -n 20
5405 ./run/initramfs/ro/lib/systemd
5967 ./run/initramfs/ro/usr/share
5967 ./usr/share
10522 ./lib
10522 ./run/initramfs/ro/lib
11729 ./run/initramfs/ro/usr/lib/python2.7
11730 ./usr/lib/python2.7
14505 ./run/initramfs/ro/usr/bin
14505 ./usr/bin
16384 ./run/log
16384 ./run/log/journal
16384 ./run/log/journal/dea1e5709c3049c0a46093ab670ffd23
31306 ./run/initramfs/ro/usr/lib
31307 ./usr/lib
55996 ./run/initramfs/ro/usr
55998 ./usr
70830 ./run/initramfs/ro
77300 ./run/initramfs
94224 ./run
165260 .That was when I got this awesome tidbit from irc:
<niceguy> so the BMC is a bit weird because it's an embedded device. In embedded linux, we usually try to limit the amount of writing to flash storage to avoid wearing it out, allow powerloss without filesystem corruption, etc <niceguy> mtdblock4 is the root file system as orgially flashed. It's read only. it'll always show it's full; you can't write to it mtdblock5 is a writeable parttion. <niceguy> the cow filesystem type for / combines mtdblock4 and mtdblock5 together. This gives the benefits of a read-only root filesystem that can't be corrupted with a writable file system that you can edit <niceguy2> The login credentials for SSH and the Web GUI are shared ? changing one will change the other. This makes it easy to change your BMC root password from a Web browser on a second computer if required.
So I don't need to delete any files, but I might as well try to change the password from the web interface. When I tried to log into the Talos II web interface, which I could before, now I can't:
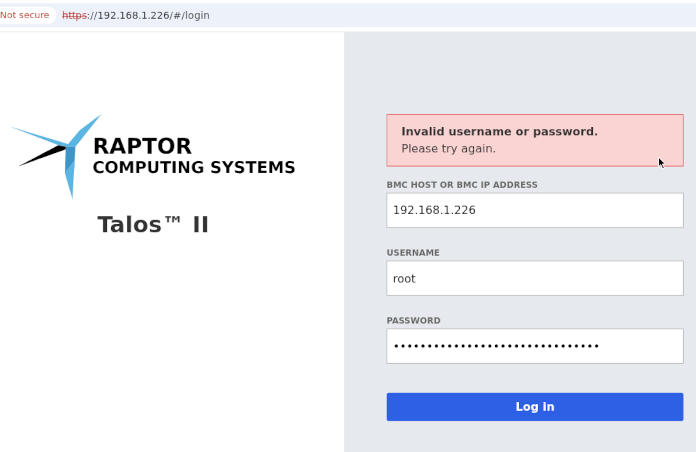
At this point, I don't know how to change the OpenBMC's root password, BUT if you have physical access to our computer and connect via serial and you manage to guess my password, would you mind telling me what it is? ????
Thankfully, before I deleted/disabled the OpenBMC's root password, I forced the BCM's sshd to only allow ssh key logins. It's actually fairly easy to do this. You first make sure that you can login without typing in the BMC's password.
joshua@dobby.lan:~/ $ ssh-copy-id root@talos-bmc.local
Once that command succeeds, you'll now be able to type into the server via typing in your ssh key's (~/.ssh/id_rsa) password. If you set up the ssh agent at login, like OpenBSD does by default (eval `ssh-agent -s`), then you don't even have to type in your ssh keys!
root@talos-bmc.local:/etc/ssh/ $ grep 'PasswordAuthentication no' -C 1 sshd_config
root@talos-bmc.local:/etc/ssh/ $ reboot
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication no
PermitEmptyPasswords noI told the BMC to reboot, then I doubled checked that password authentication was disabled via creating a new user on my laptop: "jab". Then I was very happy to watch this command fail:
joshua@dobby.lan:~/ $ doas -u jab ssh root@talos-bmc.local
root@192.168.1.226: Permission denied (publickey).For some reason, I asked myself?do I really know that jab cannot login to the talos II? Let's allow password login. Maybe that'll do something?
root@talos-bmc.local:/etc/ssh/ $ grep 'PasswordAuthentication no' -C 1 sshd_config
root@talos-bmc.local:/etc/ssh/ $ reboot
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication yes
PermitEmptyPasswords yesBUT now jab can log into the BMC with no password! WHAT!?
jab@dobby.lan:/doas $ ssh root@talos-bmc.local "echo hello there!"
echo hello there!I switched to a tty, logged in as jab to see if jab could login to the BMC without doas. Will this command prompt me for the root password?
jab@dobby.lan:~/ $ ssh root@talos-bmc.local "echo hi partner!"
hi partner!WHAT!? Did user jab somehow copy user joshua's ssh keys?
jab@dobby.lan:/home/jab $ cd .ssh
/bin/sh: cd: /home/jab/.ssh - No such file or directoryWhat a second, jab can log in as root, because root has an empty password! How did I do that? Maybe I did a passwd -d root && passwd -u root? I've honestly no idea. On a whim, I tried to change the BMC password again, and it finally worked?but I chose a really really poor password. It was not very secure.
jab@dobby.lan:~/ $ ssh root@root@192.168.1.226
root@talos:~/ # passwd
New password: ******
Retype new password: ******
Password changed successfullyFor now, we will keep the talos's BMC having a non-default and slightly insecure password. It's time to try to update the blackbird's firmware.
Updating the firmware for the blackbird
Now that we have the firmware updated for the Talos II, it's time to do the same for the blackbird!
I have a com port (serial cable) set up with the blackbird and I am currently viewing the blackbird from a serial connection. At the moment, our blackbird has a default password of 0penBmc, and there seems to be something fishy going on, as this graphic sort of shows.
What is the current blackbird's firmware version? I see that the blackbird's IP address is 192.168.1.218. Maybe I can log into the web interface for the BMC, which is https://192.168.1.218 ? The web interface says what the firmware version is. I directed my browser to blackbirdIPAddress and and Chrome said, "192.168.1.217 redirected you too many times." So maybe there is a web server there, but it's having trouble sending the interface?
That's fine. How else can I find out what firmware the blackbird is using? Well, according to this table, I can look at the /etc/os-release file.
ssh -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedAlgorithms=+ssh-rsa root@blackbird-bmc.local
root@blackbird-debian:~/ $ cat /etc/os-release | grep BUILD_ID
BUILD_ID="20190510193021"Consulting the blackbird firmware web page, that date matches system package 1.00.
Let's update the blackbird's firmware to the latest version 2.10. Let's go ahead and download the latest firmware and verify it. Apparently the "gpg: WARNING:" is normal.
joshua@dobby.lan:~/Downloads/firmware $ gpg --verify blackbird-pnor-v2.10-bundle.tar.asc 2>&1
joshua@dobby.lan:~/Downloads/firmware $ gpg --verify blackbird-openbmc-v2.10-bundle.tar.asc \
Blackbird-openbmc-v2.00-bundle.tar 2>&1
gpg: assuming signed data in 'blackbird-pnor-v2.10-bundle.tar'
gpg: Signature made Thu Feb 15 19:08:30 2024 EST
gpg: using RSA key A5D08A2F2240E0B8F90945B7A8808B68FBBEBF23
gpg: issuer "support@raptorcs.com"
gpg: Good signature from "Raptor Computing Systems Firmware Signer (2024) (2024 Firmware Signer) <support@raptorcs.com>" [unknown]
gpg: WARNING: The key's User ID is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: A5D0 8A2F 2240 E0B8 F909 45B7 A880 8B68 FBBE BF23
gpg: Signature made Thu Feb 15 19:08:15 2024 EST
gpg: using RSA key A5D08A2F2240E0B8F90945B7A8808B68FBBEBF23
gpg: issuer "support@raptorcs.com"
gpg: Good signature from "Raptor Computing Systems Firmware Signer (2024) (2024 Firmware Signer) <support@raptorcs.com>" [unknown]
gpg: WARNING: The key's User ID is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: A5D0 8A2F 2240 E0B8 F909 45B7 A880 8B68 FBBE BF23This took a while to figure out because
joshua@dobby.lan:~/Downloads/firmware $ gpg --verify blackbird-openbmc-v2.00-bundle.tar.asc \
Blackbird-openbmc-v2.00-bundle.tar 2>&1
gpg: Signature made Thu Feb 20 17:06:29 2020 EST
gpg: using RSA key ED0AB3BA06F5A035
gpg: Can't check signature: No public keyI also went looking for the checksum of the file, because when you verify Debian images you also [verify the checksum](https://wiki.debian.org/VerifyISOImage). A very helpful hacker on #talos-workstation told me that, Debian's verify data integrity way is just different. They cryptography sign the checksum file, because that's less hardware intensive. Guix as per usual, does things the *right* and *easy* way, which requires one [command](https://guix.gnu.org/manual/en/html_node/USB-Stick-and-DVD-Installation.html) to very the downloaded file.
joshua@dobby.lan:~/Downloads/firmware $ bzip2 -d blackbird-v2.00-image-bmc.bz2
joshua@dobby.lan:~/Downloads/firmware $ mv blackbird-v2.00-image-bmc image-bmc
ssh-copy-id seems to work, but I still have to enter my password everytime I ssh into the BMC.
This fails. to run.
joshua@dobby.lan:~/Downloads/firmware $ scp image-bmc root@192.168.1.217:/run/initramfs/image-bmc 2&>1
<bobpaul> scp has an option to use the non-sftp protocol [16:01] [Libera] <bobpaul> Modern scp uses sftp on the remote side, but the old protocol only needs ssh and I think cat [16:02]
joshua@dobby.lan:~/ $ scp -O image-bmc root@blackbird-bmc:/run/initramfs/image-bmc
joshua@dobby.lan:~/ $ ssh -o HostKeyAlgorithms=+ssh-rsa \
-o PubkeyAcceptedAlgorithms=+ssh-rsa \
root@192.168.1.217
joshua@dobby.lan:~/ $ cat .ssh/config
# the talos is annoying to use right now...it must be outdated.
# this fixes it.
Host 192.168.1.217
HostKeyAlgorithms +ssh-rsa
PubkeyAcceptedKeyTypes +ssh-rsaroot@192.168.1.217:/ $ fw_printenv | grep eth1addr
eth1addr=2c:09:4d:00:0a:d1If there is a problem later on, its because I put down the same MAC address for two different ethernet NICs. But I only had one written down MAC address. fw<sub>setenv</sub> ethaddr 2c:09:4d:00:0a:d1 fw<sub>setenv</sub> eth1addr 2c:09:4d:00:0a:d1
updating the PNOR
tar -xf blackbird-pnor-v2.10-bundle.tar cd shell<sub>upgrade</sub>/ bzip2 -d blackbird-v2.10.pnor.bz2 scp -O blackbird-v2.10.pnor root@192.168.1.217:/tmp/ pflash -E -p blackbird-v2.10.pnor pflash -P CVPD -c
the serial connection on the BMC is giving me endless of these: 469.336171] aspeed-i2c-bus 1e78a440.i2c-bus: irq handled != irq. expected 0x00001001, but was 0x00000001 [Libera] <bobpaul> ??\<sub>(???)</sub>_/?? [16:32] <ljrBridge> [Libera] <bobpaul> Aspeed is on the dpga [16:35] <ljrBridge> [Libera] <bobpaul> *fpga <ljrBridge> [Libera] <bobpaul> That's documents for v1 https://wiki.raptorcs.com/wiki/Blackbird/Firmware [16:38] <ljrBridge> so much so that it is hard to log in via the serial connection. It's actually easier to ssh into the BMC right now.
I am trying to change the default BMC password for the blackbird. Finally I can ssh root@blackbirdBMC without needing a password!
joshua@dobby.lan:~/ $ passwd -u root
joshua@dobby.lan:~/ $ passwd root # typed in new password
joshua@dobby.lan:~/ $ # passwd was not changed
joshua@dobby.lan:~/ $ passwd -d root
joshua@dobby.lan:~/ $ passwd # typed in new password
joshua@dobby.lan:~/ $ # root password change was denied.
BUT this now works: doas -u jab ssh root@blackbird-bmc:/, which means the root password is now: "".
I tried multiple combinations of passwd -u root and passwd root. The password for the root account failed to change. So I told the BMC to reboot.
Debricking the BMC
As an aside, if somehow, you have a bricked BMC, that does not let you ssh into it, BUT you do have a working uboot, you can still debrick the BMC!
You definitely want to remember the machine's mac addresses. Here's how you would copy those out.
joshua@192.168.1.220:~/ $ ip link show | grep -A 2 enP4
2: enP4p1s0f0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000
link/ether 2c:09:4d:00:08:9e brd ff:ff:ff:ff:ff:ff
altname enx2c094d00089e
3: enP4p1s0f1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000
link/ether 2c:09:4d:00:08:9f brd ff:ff:ff:ff:ff:ff
altname enx2c094d00089f:ID: b120decc-a9f8-48f5-8985-aaaa2a80a0ad